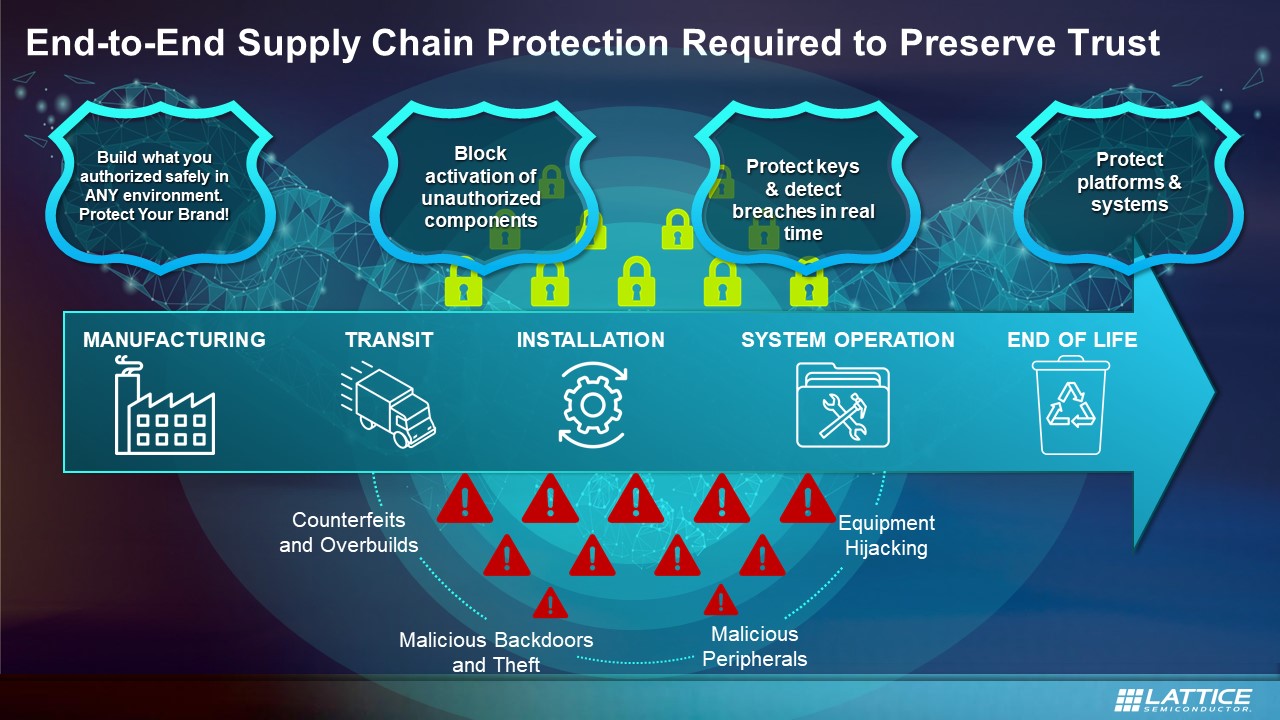
Upcoming Strategy to Outline Agency's Supply Chain Security Approach > U.S. Department of Defense > Defense Department News

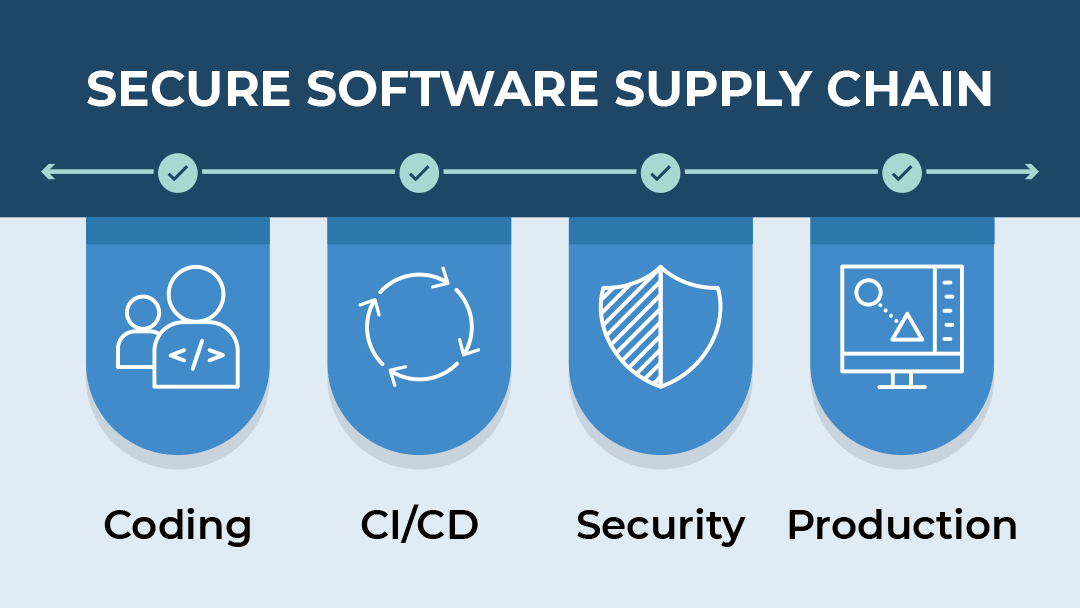
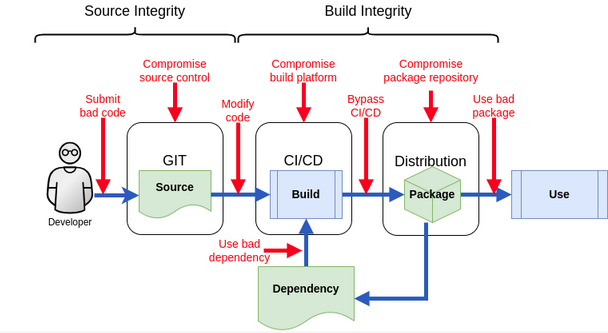
Software projects face supply chain security risk due to insecure artifact downloads via GitHub Actions | CSO Online
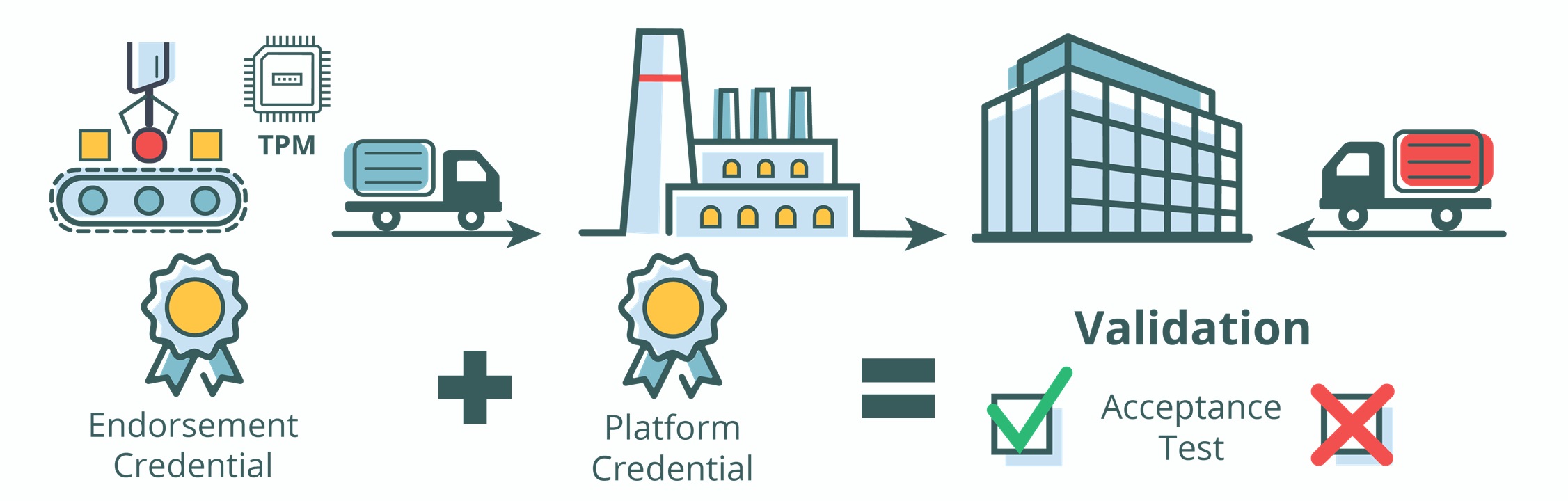
New Software Helps to Mitigate Supply Chain Management Risk > National Security Agency/Central Security Service > Article