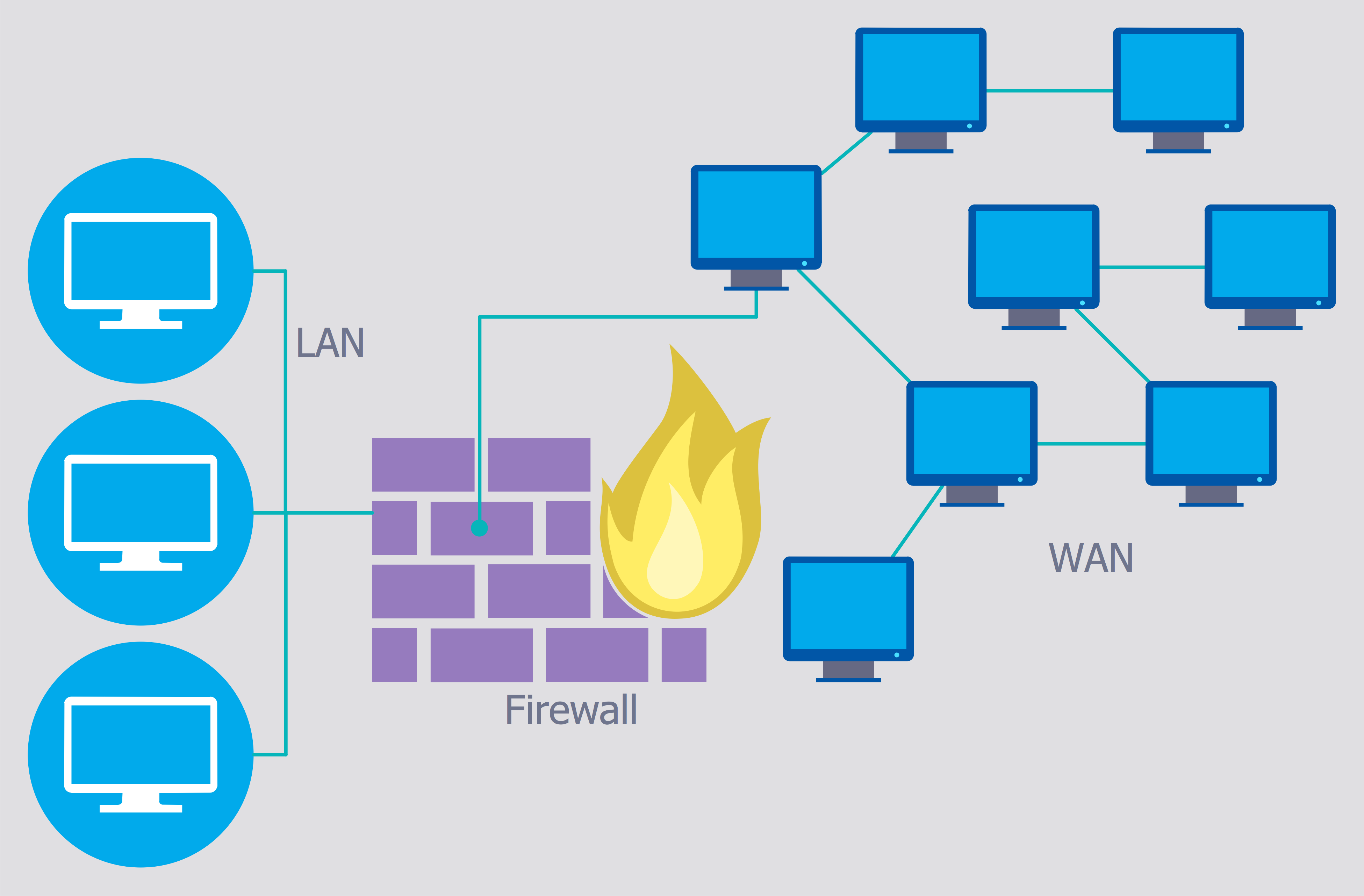
Amazon.com: Data Security in Cloud Storage (Wireless Networks): 9789811543739: Zhang, Yuan, Xu, Chunxiang, Shen, Xuemin Sherman
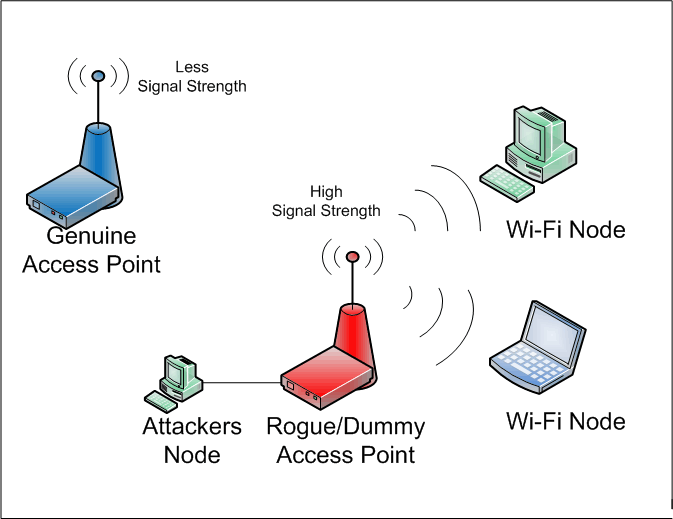
Network Security : WiFi Security fixation | Pune Mumbai Hyderabad Delhi Bangalore India | Valency Networks

Premium Vector | Data security design concept internet data exchange technology digital information protection service different device secure data transmission abstract wireless safe database vector illustration